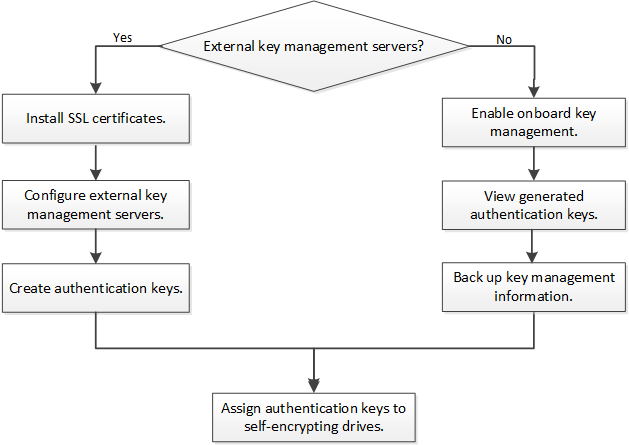
Hardware-based encryption workflow
You must configure key management services before the cluster can authenticate itself to the self-encrypting drive. You can use an external key management server or an onboard key manager.
Give documentation feedback