Mutual authentication of CSR
To establish mutual authentication between the CMM and an external LDAP server, have the CMM certificate-signing request (CSR) signed by an outside Certificate Authority (CA) using the CMM management interface.
To generate a CSR on the CMM and get it signed by using the CMM web interface, complete the following steps:
- Start a CMM web interface session.
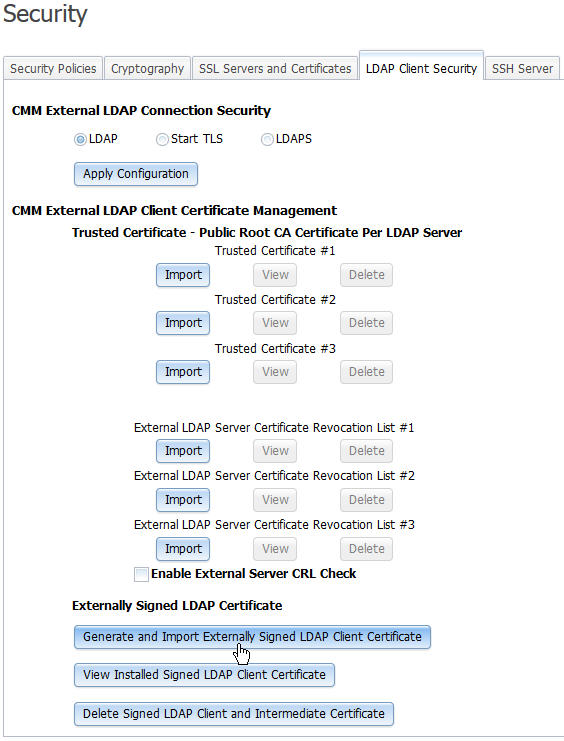
- Click Mgt Module Management > Security and select the LDAP Client Security tab.
- Select the option to either import, or paste certificate information, then click Apply Import.
To generate a CSR on the CMM and get it signed by using the CMM CLI, complete the following steps:
- Start a CMM CLI session (see Starting the command-line interface for instructions).NoteThe
sslcfg command must be targeted to the primary CMM. The following example assumes that the command environment has been set to the primary CMM through the env command (see env command for information about command use). If the command environment has not been set to the primary CMM, you can direct the command to the primary CMM by using the -T mm[p] option (see Command targets for information). - Generate the CSR on the CMM by using the CMM CLI sslcfg command (see sslcfg command for additional information about command use):
sslcfg -gen csr -c "<em className="ph i">country</em>" -sp "<em className="ph i">state</em>" -cl "<em className="ph i">city</em>" -on "<em className="ph i">org</em>" -hn <em className="ph i">hostname</em>The required options are as follows:
- country is two-character alphabetic code for the country, in double quotation marks.
- state is a state or province name of up to 60 characters in length, in double quotation marks.
- city is a city or locality name of up to 50 characters in length, in double quotation marks.
- org is an organization name of up to 60 characters in length, in double quotation marks.
- hostname is a valid host name of up to 60 characters in length.
NoteYou can specify additional optional fields for the CSR, if needed (seesslcfg command for additional information). - Download the CMM CSR to the specified server by using the CMM CLI sslcfg command. Depending on your CMM configuration, supported server types can include TFTP, FTP, HTTP, HTTPS, and SFTP. See sslcfg command for additional information about command use.
sslcfg -dnld csr -u <em className="ph i">URL_of_location_to_put_file</em>where URL_of_location_to_put_file is a fully qualified location that specifies the server type, the IPv4 or IPv6 IP address of the server, and a valid file name of up to 256 characters and containing any character except the percent sign ( % ), forward slash ( / ), or double quotation marks ( " ).
NoteFor information about how to specify a URL for file transfer, seeSpecifying a URL for file transfer. - Using the approved procedure for your organization, sign the CSR; then, place the signed certificate on a TFTP server for uploading.
- Import the signed certificate to the CMM by using the CMM CLI sslcfg command (see sslcfg command for additional information about command use):
sslcfg -upld -u <em className="ph i">URL_of_certificate_location</em>where URL_of_certificate_location is a fully qualified location that specifies the IPv4 or IPv6 IP address of the server and a valid file name, of up to 256 characters and containing any character except the percent sign ( % ) or double quotation marks ( " ). The forward slash ( / ) can be used only as part of the path name, not as part of the file name.
NoteFor information about how to specify a URL for file transfer, seeSpecifying a URL for file transfer. - Make sure that the certificate or the certificate chain of the entity that signed the new CMM LDAP client certificate is imported into the LDAP server. This makes sure that the LDAP server trusts the certificate (see the documentation for your LDAP server for information and instructions).
- Note that this procedure allows the external LDAP server to trust the CMM, but not any other management components in the Lenovo Flex System chassis. For the external LDAP server to trust other management components, such as IMMs, import the CA into the external LDAP server, following the steps in Mutual authentication using CA, or, if the chassis policy allows, export a CSR from each management component, get it signed, and import it back into the corresponding Lenovo Flex System chassis management component.