Configuring NIST 800-131A compliance
The CMM can be configured to enforce NIST 800-131A cryptography for compute nodes in the chassis managed by the CMM and the CMM itself.
The CMM supports the National Institute of Standards and Technology (NIST) SP 800-131A compliance framework. This provides stricter cryptography options for the CMM and compute nodes in the chassis that are managed by the CMM. I/O modules are not presently subject to NIST compliance.
Two NIST mode settings are available for the Flex System chassis, Compatibility and NIST SP 800-131A. The default Compatibility setting enforces no restrictions on the allowed key lengths and algorithms. The NIST SP 800-131A setting only allows key lengths and algorithms acceptable by NIST SP 800-131A recommendations.
- X.509 certificates and their associated keys (CMM CA certificate, CMM certificate, compute node certificates, external LDAP certificates)
- CMM SSH server private key and user SSH public keys
- SNMPv3 user authentication and privacy algorithms selected in the CMM user interface
- Features on Demand (FoD) licenses on the CMM
- External LDAP X.509 certificates or externally signed CMM Web certificate
- SNMPv3 user authentication or privacy algorithms selected in the CMM user interface
- Features on Demand (FoD) licenses on the CMM
- Legacy: No enforcement, SSL 3.0, TLS 1.0, TLS 1.1 and TLS 1.2 are allowed.
- TLS 1.2 Server Only: Server applications on the CMM are restricted to TLS 1.2.
- TLS 1.2 Server and Client: Server and client applications on the CMM are restricted to TLS 1.2.
- Automatic certificate regeneration using NIST SP 800-131A compliant key lengths and hash algorithms: If a chassis CA certificate is imported into the browser trust store before changing to NIST SP 800-131A mode, when using a web interface to connect to a device in the chassis such as a compute node or CMM, a message about an untrusted server certificate will be displayed. To continue accessing the web interface, a new chassis CA certificate must be imported into the trust store. It is recommended that you do not ignore the untrusted server certificate message.
- Automatic SSH server keys regeneration using NIST SP 800-131A compliant key lengths: If you connected to the CMM using SSH protocol and added the SSH server to the CMM known hosts list before changing to NIST SP 800-131A mode, when connecting to the CMM through SSH after changing to NIST 800-131A mode, an error message will be displayed about server keys mismatch. To access the CLI using SSH, the CMM known host list must be updated with the new SSH server keys.
- Automatic selection of the algorithms used for encryption and hashing operations: To maintain NIST SP 800 -131A compliance, the selection of algorithms for all encryption is centrally-managed by the CMM, and strictly follows the cryptographic NIST SP 800-131A mode. Some protocols implemented on the CMM are not NIST SP 800-131A compliant. This is because some protocols strictly define the algorithm to be used. The following is a list of exceptions from the NIST 800-131A requirements, determined by the algorithm used:
- SHA1 hashing algorithm can be used for SNMPv3 authentication while in NIST SP 800-131A mode.
- SHA1 hashing can be used for IPMI while in NIST SP 800-131A mode.
- User configured TSL/SSL: The NIST SP 800-131A mode setting is activated only when the SSL/TLS mode is set to either TLS 1.2 Server and Client or TLS 1.2 Server Only. The TLS 1.2 Server Only option is only valid on the CMM. This is required to make sure that all TLS/SSL connections between chassis components or between chassis components and external entities meet the cryptographic requirements of NIST SP 800-131A. Setting this option to TLS 1.2 Server Only will cause the chassis to be placed in NIST SP 800-131A Custom mode, instead of the NIST SP 800-131A Strict mode. Consider the following guidelines about the limitations and possible effects of each TLS/SSL setting:
- Legacy: All TLS/SSL capable servers and clients use the default configuration. No functional limitation should be noticed by the user.
- TLS 1.2 Server Only: This value can be only be selected on the CMM. All TLS/SSL capable servers are configured to use only TLS 1.2. The user might not be able to connect to a component web interface, unless the web browser supports TLS 1.2. The latest versions of Internet Explorer and Chrome browsers support TLS 1.2, however in Internet Explorer support has to be enabled explicitly. Firefox supports TLS 1.2 beginning with version 27. Client connections from chassis components to external TLS/SSL capable servers should not be affected in any way.
- TLS 1.2 Server and Client: All TLS/SSL capable servers are configured to use only TLS 1.2. The user might not be able to connect to a component web interface unless the web browser supports TLS 1.2. The latest versions of Internet Explorer and Chrome browsers support TLS 1.2, however, support in Internet Explorer must be enabled explicitly. Firefox supports TLS 1.2 beginning with version 27. All client connections from chassis components to external TLS/SSL capable servers are configured to use TLS 1.2. If the external TLS/SSL capable servers do not support TLS 1.2, all client connections to those servers will fail. This limitation affects client connections for file transfer and authentication to external TLS/SSL capable LDAP servers. If the chassis is configured to use external authentication only and the external LDAP severs support TLS/SSL connections, but do not support TLS 1.2, setting the TLS 1.2 Server and Client value causes the user to be logged out and lose access to all chassis components. In this case it is recommended that you use the TLS 1.2 Server Only option.
You can set the cryptography mode for the CMM through the CMM web interface or from the command-line interface (CLI). To set the cryptography mode for the CMM through the CLI, use the crypto command. See crypto command for information.
To set the cryptography mode for the CMM through the web interface, use the following procedure:
- From the CMM web interface click Mgt Module Management > Security > Cryptography.
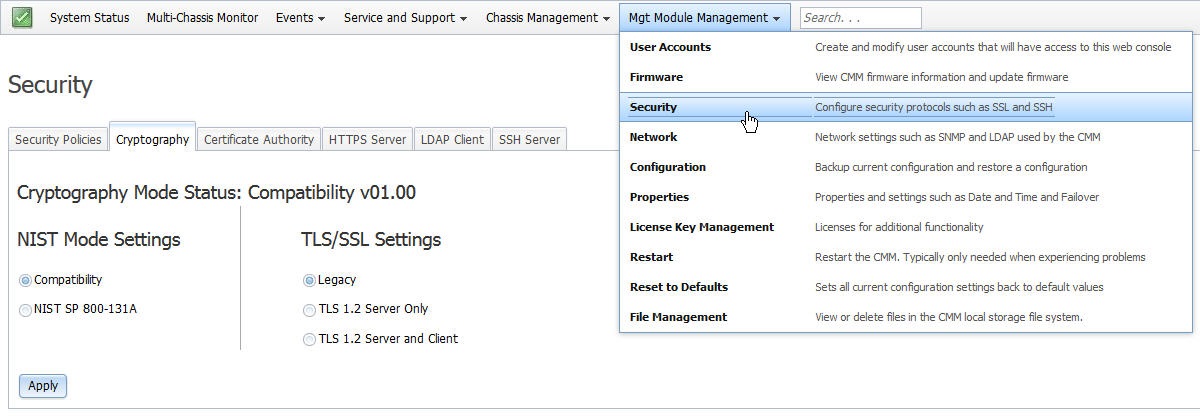
- Select NIST SP 800-131A. The options for TLS/SSL settings will then be restricted to the following options, of which the user must select one:
- TLS 1.2 Server Only: Starts the creation of waivers for uncompliant items.
- TLS 1.2 Server and Client: Required option for the chassis to achieve NIST SP 800-131A Strict compliance.
NoteThe option for Cipher Strength located atMgt Module Management > Security > Certificate Authority is automatically restricted to RSA2048-SHA256, which is the only NIST SP 800-131A compliant option. - Click Apply and a cryptographic mode change message warning is displayed, stating that changing the cryptographic mode will reboot the CMM, but changing the TLS/SSL settings will only restart the associated services, and that both situations make the web interface unusable while processing. Click OK to make the change.
- Restart the CMM for the changes to take effect. After restarting the CMM, check for uncompliant settings that are not automatically changed on the CMM. Each uncompliant setting will generate a waiver and the mode will be set to NIST SP 800-131A Custom. In this mode, new uncompliant cryptographic items cannot be configured on the CMM. If no waivers are generated, the mode will be NIST SP 800-131A Strict, and the Cryptography tab will indicate the mode.
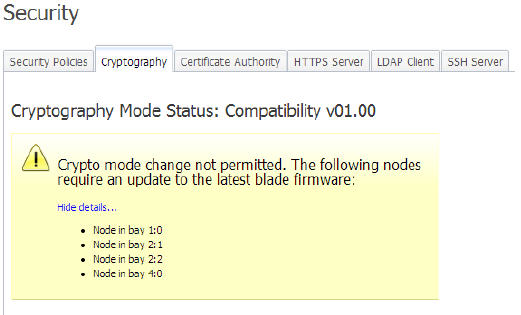
 NoteIf all compute nodes and
NoteIf all compute nodes andCMMs in the chassis do not have firmware that supports NIST SP 800-131A compliance, the mode change will fail and a message will appear, indicating the nodes that have uncompliant firmware.