Configuring cryptography management
Use this topic to understand the purpose of cryptography management and how to configure the cryptography mode for the IMM2 firmware.
The purpose of any cryptography is to ensure the confidentiality, authenticity and integrity of data. These goals are achieved with the use of cryptography keys. Cryptography is a method of storing and transmitting data in a particular form so that only those for whom the data is intended can read and process it.
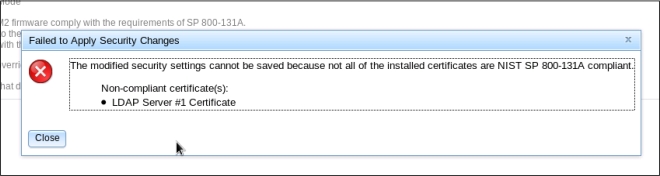
- Basic Compatibility Mode
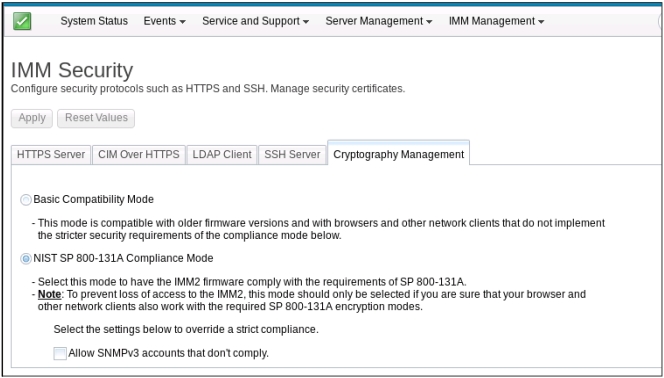
- NIST SP 800-131A Compliance Mode
The Basic Compatibility Mode is compatible with older firmware versions and with browsers and other network clients that do not use the NIST SP 800-131A Compliance mode.
The Cryptography Management tab with the Basic Compatibility Mode selected is shown in the following illustration.
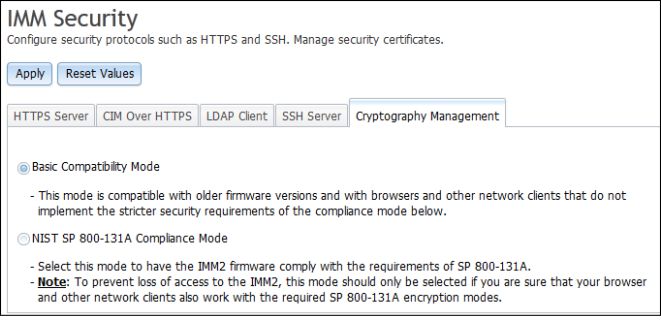
- To prevent loss of access to the IMM2, use the NIST SP 800-131A Compliance Mode only if you are sure that your browser and other network clients can work with the SP 800-131A encryption modes.
- When using the NIST SP 800-131A Compliance Mode, you can allow SNMPv3 accounts to disobey the restrictions set by this mode.
The Cryptography Management tab with the NIST SP 800-131A Compliance Mode selected is shown in the following illustration.
- Log in to the IMM2.
- Click the Security option under the IMM Management tab.
- Click the Cryptography Management tab.
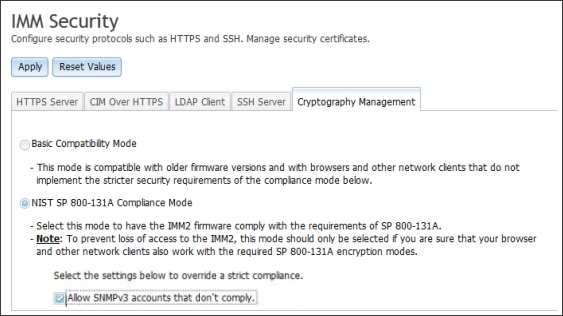
Select the cryptography mode on the Cryptography Management page; then, click the Apply button. You are asked for confirmation as shown in the following illustration.
If the IMM2 has compatible certificates and SSH Keys, the Cryptography mode is set to the NIST-800-131A Compliance Mode as shown in the following illustration.
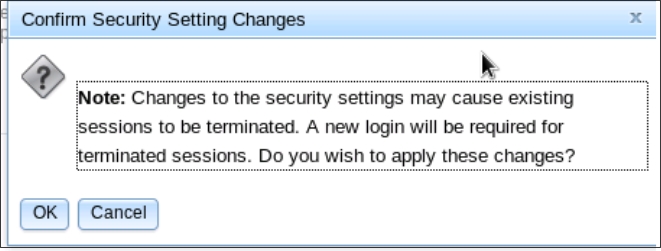
If the installed certificates are not NIST-800-131A compliant the security settings cannot be changed as shown in the following illustration.