Configuring the SKLM Feature on Demand option
This topic provides information about the Security Key Lifecycle Manager (SKLM) software product that is used for creating and managing security keys.
The Security Key Lifecycle Manager (SKLM) is a software product for creating and managing security keys. The SKLM for System x Self Encrypting Drives (SED) - Features on Demand (FoD) option is a System x FoD option that enables centralized management of encryption keys. The encryption keys are used to gain access to data stored on SEDs in a System x server.
A centralized SKLM (key repository) server provides the encryption keys to unlock the SEDs in the System x server. The FoD option requires that a FoD Activation key be installed in the IMM2 FoD key repository. The Activation key for the FoD option is a unique identifier comprised of the machine type and serial number. To use the storage key/drive access functionality, the FoD key System x TKLM Activation for Secure Drive Encryption (Type 32796 or 801C) must be installed in the IMM2 FoD key repository. See Features on Demand for information pertaining to installing an activation key.
The SKLM FoD option is limited to System x IMM2-based servers. To increase security, the IMM2 can be placed in a separate management network. The IMM2 uses the network to retrieve encryption keys from the SKLM server; therefore, the SKLM server must be accessible to the IMM2 through this network. The IMM2 provides the communication channel between the SKLM server and the requesting System x server. The IMM2 firmware attempts to connect with each configured SKLM server, stopping when a successful connection is established.
- A valid FoD activation key is installed in the IMM2.
- One or more SKLM server hostname/IP addresses are configured in the IMM2.
- Two certificates (client and server) for communication with the SKLM server are installed in the IMM2.
A Transport Layer Security (TLS) connection must be established between the IMM2 and the SKLM server. The IMM2 authenticates the SKLM server by comparing the server certificate submitted by the SKLM server, with the SKLM server certificate previously imported into the IMM2's trust store. The SLKM server authenticates each IMM2 that communicates with it and checks to verify that the IMM2 is permitted to access the SKLM server. This authentication is accomplished by comparing the client certificate that the IMM2 submits, with a list of trusted certificates that are stored on the SKLM server.
- Open a web browser. In the address or URL field, type the IP address or host name of the IMM2 to which you want to connect.
- Type your user name and password in the IMM2 Login window.
- Click Log In to start the session.
- Navigate to the top of the IMM2 window and locate the tabs below the title bar.
- Click the Security option under the IMM Management tab.
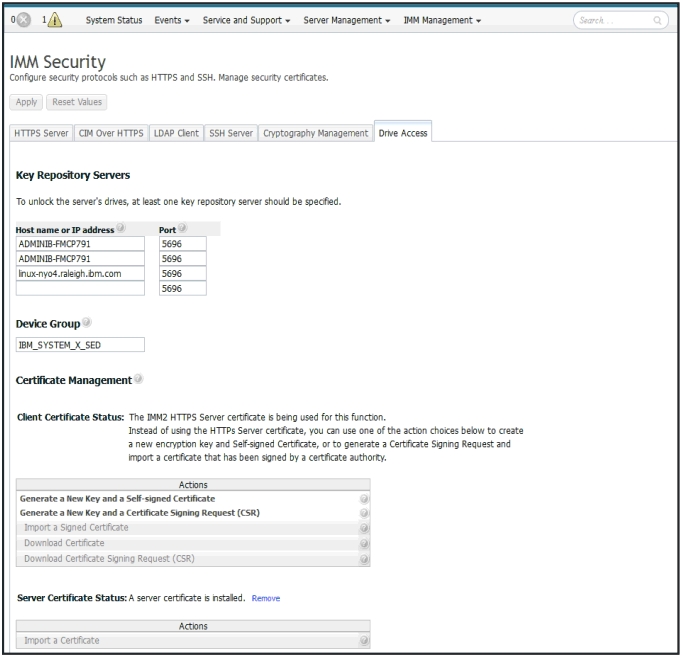
- Click the Drive Access tab on the IMM Security page.
- Key Repository Servers
- Device Group
- Certificate Management
- The Drive Access tab is not displayed if the SKLM FoD activation key is not installed in the IMM2.
- Additional information for the SKLM software product can be found at IBM Security Key Life Cycle Manager.
- The encryption key created by the SKLM server is associated with the System x server Universal Unique Identifier (UUID), machine type, and serial number. If the system board is replaced, the UUID, machine type, and serial number must be restored during the service procedure. The UUID, machine type, and serial number are necessary to obtain an existing key required for access to the SEDs. Information pertaining to restoring the UUID, machine type, and serial number can be found in the documentation for your server and by searching on the keywords updating the Universal Unique Identifier or searching on the keyword UUID.