Creating a custom role
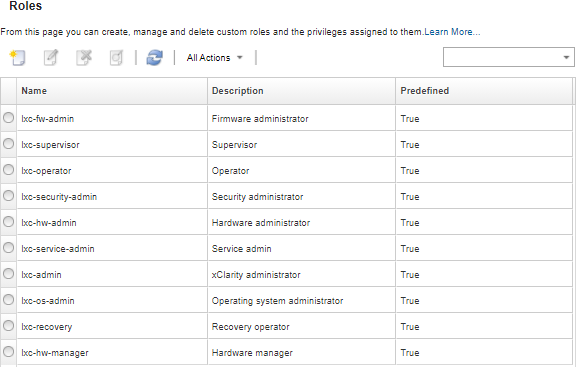
A role is a set of privileges, or permissions to perform a specific action. Lenovo XClarity Administrator includes several predefined (default) roles. You can also create custom roles that enforce a unique set of privileges that users can perform
Before you begin
You must have lxc-supervisor or lxc-security-admin authority to perform this task.
About this task
For a ThinkSystem server in a rack, add the mm-power-and-restart-access-v1 privilege.
For an entire Flex System chassis (including devices in the chassis), add the mm-power-and-restart-access-v1 privilege.
For a ThinkSystem server in a chassis, add mm-power-and-restart-access-v1, mm-blade-operator-v2, and the mm-blade-#-scope-v2 privilege that matches the target server.
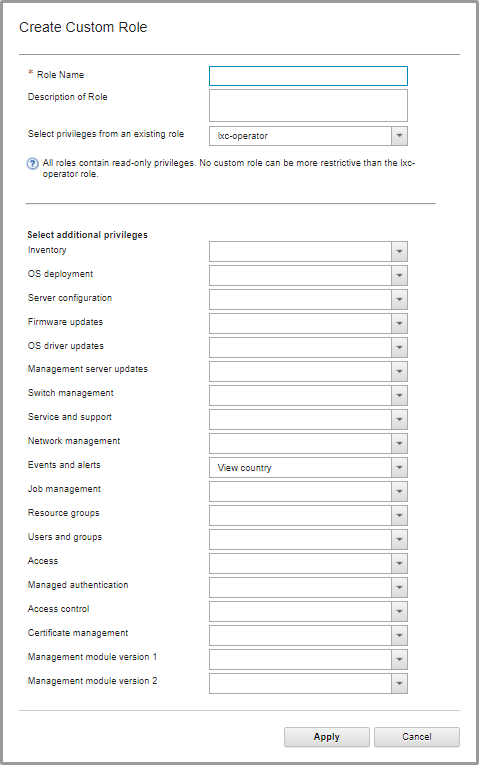
All roles contain read-only privileges. No custom role can be more restrictive than the lxc-operator role.
If a user is does not have privileges to perform specific actions, menu items, toolbar icons, and buttons that perform those actions are disabled (greyed out).
XClarity Administrator provides a role group for each predefined role, using the same name as the role. Consider creating a role group for new roles that you create. For more information about role groups, see Creating a custom role group.
- lxc-supervisor. Users that are assigned this role can access, configure, and perform all available operations on the management server and all managed devices.
Users that are assigned this role always have access to all managed devices. You cannot restrict access to devices for this role.
- lxc-admin. Users that are assigned this role can modify non-security related settings and perform all non-security related operations on the management server, including the ability to update and restart the management server. This role also provides the ability to view all configuration and status information about the management server and managed devices.
lxc-security-admin. Users that are assigned this role can modify security settings and perform security-related operations on the management server and managed devices. This role also provides ability to view all configuration and status information about the management server and managed devices.
Users that are assigned this role always have access to all managed devices. You cannot restrict access to devices for this role.
- lxc-hw-admin. Users that are assigned this role can modify non-security settings and perform non-security related operations on managed devices, including the ability to update and restart managed devices. This role also provides the ability to view all configuration and status information about the management server and all managed devices.
- lxc-fw-admin. Users that are assigned this role can create firmware policies and deploy those policies to managed devices. Users that are not assigned this role can only view policy information.
- lxc-os-admin. Users that are assigned this role can download and deploy operating systems and device-driver updates to managed servers. Users that are not assigned this role can only view operating-system and device-driver information.
- lxc-service-admin. Users that are assigned this role can collect and download service files for XClarity Administrator and managed devices. Users that are not assigned this role can collect but not download service data.
- lxc-hw-manager. Users that are assigned this role can discover new devices and place those devices under the management control of the XClarity Administrator. This role prohibits users from performing operations or modifying configurations settings on the management server and managed devices beyond those operations that are necessary to discover and manage new devices.
- lxc-operator. Users that are assigned this role can view all configuration and status information about the management server and managed devices. This role prohibits users from performing operations or modifying configurations settings on the management server and managed devices.
lxc-recovery. Users that are assigned this role can modify security settings and perform security-related operations on the management server. These users can also authenticate directly to the XClarity Administrator even if the authentication method is set to external LDAP server. This role provides a recovery mechanism in case a communication error occurs with the external LDAP server that uses the
Login Credentials
configuration.Users that are assigned this role always have access to all managed devices. You cannot restrict access to devices for this role.
- lxc-sysrdr
- lxc-sysmgr
Procedure
To create a custom role, complete the following steps.
Results
- View the privileges associated with a specific role by selecting the role and clicking the View icon (
 ).
). - Rename or edit the custom role by clicking the Edit icon (
 ). When you edit a custom role, you can change selected privileges, the description, and list of users that are associated with the role.NoteYou cannot modify a predefined role
). When you edit a custom role, you can change selected privileges, the description, and list of users that are associated with the role.NoteYou cannot modify a predefined role - Delete the predefined or custom role by clicking the Delete icon (
 ).
). - Add or remove roles from a role group (see Adding and removing multiple users from a role group).
- Restore all predefined roles that were deleted by clicking .