Installing a trusted, externally-signed server certificate for XClarity Management Hub for edge-client devices
You can choose to use a trusted server certificate that was signed by a private or commercial certificate authority (CA). To use an externally-signed server certificate, generate a certificate signing request (CSR), and then import the resulting server certificate to replace the existing server certificate.
Before you begin
- If you install an externally-signed Lenovo XClarity Management Hub server certificate using a new root CA, XClarity Management Hub loses its connection to the managed devices, and you must re-manage the devices. If you install an externally-signed Lenovo XClarity Management Hub server certificate without changing the root CA (for example, when the certificate is expired), there is no need to re-manage the devices.
- If new devices are added after the CSR is generated and before the signed server certificate is imported, those devices must be restarted to receive the new server certificate.
About this task
As a best practice, always use v3 signed certificates.
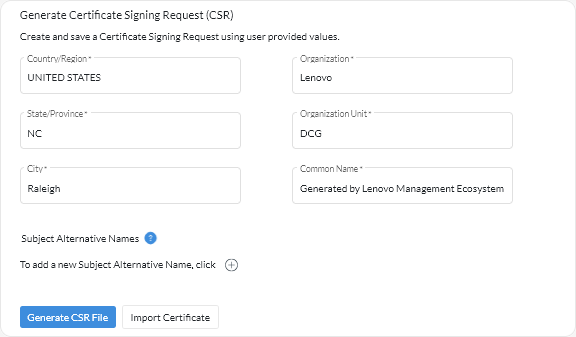
The externally-signed server certificate must be created from the Certificate Signing Request that was most recently generated using the Generate CSR File button.
The externally-signed server certificate content must be a certificate bundle that contains the entire CA signing chain, including the CA’s root certificate, any intermediate certificates, and the server certificate.
If the new server certificate was not signed by a trusted third party, the next time that you connect to Lenovo XClarity Management Hub, your web browser displays a security message and dialog prompting you to accept the new certificate into the browser. To avoid the security messages, you can import the server certificate into your web browser's list of trusted certificates (see Importing the server certificate into a web browser for Lenovo XClarity Management Hub for edge-client devices).
XClarity Management Hub begins using the new server certificate without terminating the current session. New sessions are established using the new certificate. To use the new certificate in use, restart your web browser.
Procedure
To generate and install an externally-signed server certificate, complete the following steps.