You can choose to use a Security Assertion Markup Language (SAML) 2.0 identity provider to perform authentication and authorization for Lenovo XClarity Administrator.
Before you begin
The initial setup of XClarity Administrator must be completed before setting up the identity provider.
The following SAML
identity provider are supported.
- Microsoft Active Directory Federation Services (AD FS)
The SAML identity provider can be connected to either the management network, data network, or both. Because authentication is done through your web browser, your web browser must be able to access XClarity Administrator and the SAML server.
You can download IDP metadata using the following URL: https://<ADFS_IP_Address>/federationmetadata/2007-06/federationmetadata.xml, where <ADFS_IP_Address> is the IP address for AD FS (for example, https://10.192.0.0/federationmetadata/2007-06/federationmetadata.xml).
You must create or rename role groups in the location authentication server to match the groups that are defined in the external authentication server.
To set up an SAML identity provider, you must be logged in as a user that is a member of the lxc_admin or lxc_supervisor group.
About this task
XClarity Administrator supports using a Security Assertion Markup Language 2.0 identity provider to authenticate and authorize users. In addition to entering a user name and password, the identity provider can be set up to require additional criteria to validate a user’s identity, such as entering a PIN code, reading a smart card, and authenticating using a client certificate.
When XClarity Administrator is set up to use a identity provider, interactive login requests from the XClarity Administrator web interface are redirected to the identity provider for authentication. After the user is authenticated, the web browser is redirected back to XClarity Administrator.
If the identity provider is enabled, you can bypass the identity provider and log in to XClarity Administrator using the local or external LDAP authentication server by opening your web browser to the XClarity Administrator login page (for example, https://<ip_address>/ui/login.htm).
When XClarity Administrator is configured to use an identity provider profile, the Users Management page in the XClarity Administrator web interface is not disabled. Local user accounts are required to directly log in to a managed chassis or server (except when Encapsulation is enabled on that device) and for PowerShell and REST API authentication.
Procedure
Complete the following steps to set up an external SAML identity provider (AD FS).
- Create a recovery user account that can be used to log in to XClarity Administrator if the identity provider becomes unavailable (see Managing user accounts).
- Retrieve the identity provider (IDP) metadata from the identity provider, and save the file on the XClarity Administrator host.
- Configure the XClarity Administrator SAML client.
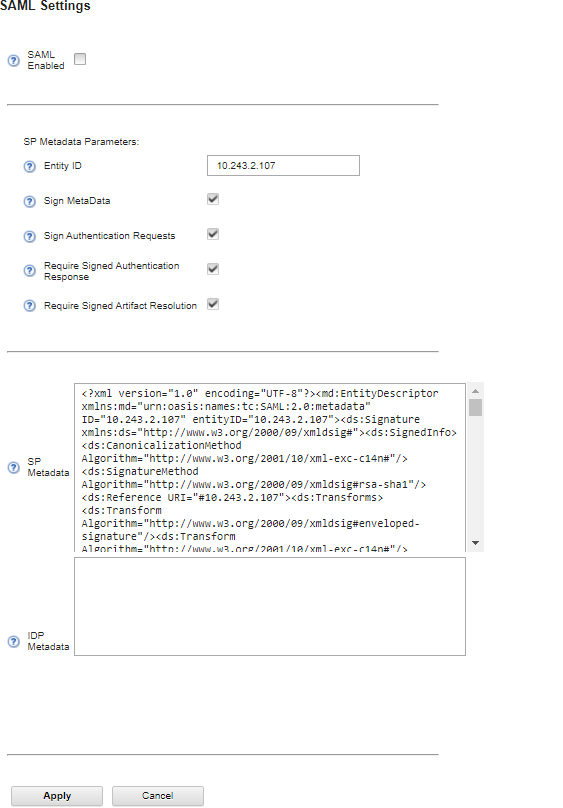
- From the XClarity Administrator menu bar, click .
- Click SAML Settings under the Users and Groups section to display the SAML Settings dialog.
- Fill in the fields on the SAML Settings page:
- Verify that the entity ID matches the IP address of the XClarity Administrator management server.
- Choose whether the generated metadata is to be digitally signed.
- Choose whether authentication requests are to be signed.
- Choose whether authentication responses must be signed.
- Choose whether the artifact-resolution requests that are sent to the remote identity provider must be signed.
- Paste the SAML identity provider (IDP) metadata that was generated by the identity provider and retrieved in step 3 into the IDP Metadata field.
- Click Apply to apply the changes and update the text in the SP Metadata field.
Do not select SAML Enabled at this point. You will enable SAML in a later step to restart XClarity Administrator.
- Copy and paste the data in the SP Metadata field to a file, and save the file with the .XML extension (for example, sp_metadata.xml). Copy this file to the AD FS host.
- Configure AD FS.
- Open the AD FS Management tool.
- Click .
- Right click Relying Party Trusts, then click Add Relying Party Trust to display the wizard
- Click Start
- On the Select Data Source page, select Import data about the relying party from a file, and then select the SP metadata file that you saved in step 3e.
- Enter a display name.
- Click Next on all pages to choose the default values.
- Click Finish to display the Claim Rules page
- Leave Send LDAP Attributes as Claims as default, and click Next.
- Enter a claim rule name.
- Select Active Directory for the attribute store.
- Add a mapping. On the left side select SAM-Account-Name, and on the right side, select Name ID for the outgoing claim type.
- Add another mapping. On the left side, select Token-Groups-Unqualified Names, and on the right side select Group for the outgoing claim type
- Click OK.
- Locate the trust that you just created in the list of Relying Party Trusts.
- Right-click the trust, and click Select properties. The trust Properties dialog is displayed.
- Click the Advanced tab, and select SHA-1 as the secure hash algorithm.
- Save the server certificate from AD FS.
- Click .
- Select the Certificate under Token-signing.
- Right-click the certificate, and click View Certificate.
- Click the Details tab.
- Click Copy to File, and save the certificate as a DER encoded binary X.509 (.CER ) file.
- Copy the server certificate .CER file to the XClarity Administrator host.
- Import the AD FS trusted certificate into XClarity Administrator web interface.
- From the XClarity Administrator menu bar, click .
- Click Trusted Certificates in the Certificate Management section.
- Click the Create icon (
 ) to add a certificate.
) to add a certificate. - Select the server certificate .CER file that you saved in the previous step.
- Click Create.
- Click SAML Settings under the Users and Groups section to display the SAML Settings dialog.
- Select SAML Enabled to enable management of user accounts using an external identity provider. When this option is selected, all user accounts exist remotely in an identity provider.
- Click Apply to apply the changes and restart the management server.
- Wait a few minutes for XClarity Administrator to restart.
Do not restart the virtual appliance manually during this process.
- Close and reopen the web browser.
- Log in to the XClarity Administrator web interface from the identity provider.
Results
The XClarity Administrator attempts to test the configuration to detect common errors. If the test fails, error messages are displayed that indicate the source of the errors.
XClarity Administrator validates the identity provider connection. If the validation passes, user authentication occurs on the identity provider when you log in to XClarity Administrator.